It started in a rugby box.
There I was, watching the match from a VIP suite—surrounded by a handful of other cybersecurity leaders. The beers were cold, the banter flowing, but one comment cut through the noise:
“Cybersecurity’s no longer about technology. It’s about sovereignty.”
That stuck with me.
That rugby-box insight wasn’t just banter—it reflected a deeper truth that’s reshaping the cyber landscape.
Because it’s true: cybersecurity has evolved from a purely technical discipline into a front line of geopolitical and economic warfare. Around the world, governments are weaponising regulation—using cyber laws to block foreign firms, force data localisation, and demand access to proprietary systems under the guise of compliance.
Suddenly, the centralised security models we’ve relied on for years are liabilities.
In this blog, I’m unpacking how the global regulatory landscape is fragmenting—and why decentralising cybersecurity, while expensive and complex, has become a strategic necessity. You’ll learn what this shift costs, where the risks lie, and how leaders can strike the right balance between compliance, control, and cost.
How Cybersecurity Regulation is Being Weaponized
Cybersecurity laws were originally designed to protect consumers and critical infrastructure, but they are now being used to:
- Impose selective enforcement on foreign businesses and political opponents.
- Create trade barriers by forcing companies to comply with complex local cybersecurity laws.
- Mandate data localization, preventing companies from storing or processing data across borders.
- Control digital infrastructure through surveillance-friendly regulations.
- Use compliance as an excuse for corporate espionage, demanding access to proprietary cybersecurity tools and encryption.
For businesses operating internationally, these tactics create a fragmented and high-risk regulatory landscape, where failure to comply can result in fines, legal battles, operational restrictions, or outright bans.
Why Centralised Cybersecurity is Becoming Risky and Costly
Many global organisations have traditionally operated with centralised cybersecurity teams, often based in major business hubs like the U.S. or Europe. This model has been efficient and cost-effective, enabling them to:
- Standardise security policies across all regions.
- Centralise talent and reduce staffing costs.
- Streamline compliance efforts with a single, unified strategy.
However, due to increasing regulatory fragmentation, a one-size-fits-all security approach no longer works. The risks and costs of maintaining a centralised security model are now outweighing the benefits in many industries. For example:
- Regulatory Fines & Compliance Risks: Cybersecurity regulations such as the GDPR (EU), China’s Cybersecurity Law, and India’s Digital Personal Data Protection Act impose steep fines for non-compliance. Non-compliance penalties can reach up to €20 million or 4% of global revenue under the GDPR. Centralised models may struggle to meet regional compliance requirements, exposing organisations to legal and financial risks.
- Restricted Cross-Border Data Transfers: Many governments prohibit organisations from storing or processing data outside national borders. This forces them to build and maintain multiple regional data centers, significantly increasing IT infrastructure costs. Organisations relying on centralised cloud providers (AWS, Google Cloud, Azure, etc.) face higher operational risks if cloud services are restricted or banned in specific regions.
- Delayed Incident Response & Security Breaches: Many regulations prevent real-time cybersecurity data sharing across borders, making it difficult for centralised teams to respond to global cyber threats. This increases the risk of prolonged breaches, reputational damage, and financial losses. Regulatory barriers limit access to global threat intelligence, reducing a company’s ability to predict and prevent attacks.
- Geopolitical Risks & Market Access Restrictions: Governments can use cybersecurity laws to ban foreign tech firms, as seen with the U.S. bans on Huawei, Kaspersky and TikTok or China’s restrictions on Western cloud providers. A centralised security model makes organisations more vulnerable to geopolitical tensions, potentially leading to forced exits from key markets.
Given these challenges, businesses are shifting toward a decentralised cybersecurity approach, despite the higher costs and complexities involved.
The Shift to Decentralised Cybersecurity: Costs vs. Risk Reduction
To reduce regulatory risks, organisations are increasingly decentralising cybersecurity operations, and moving security functions closer to the regions they serve. For example they are:
Hiring Regional Cybersecurity Talent
- Why? Regulations now require in-country expertise to manage compliance and incident response.
- Cost Impact: Companies must increase cybersecurity headcount in each region, leading to higher labour costs—especially in markets where cybersecurity talent is scarce and expensive.
- In Short: Higher costs, lower compliance risks
Establishing Regional Security Operations Centres (SOCs)
- Why? A global SOC can no longer effectively monitor threats across regulated regions.
- Cost Impact: Organisations must set up multiple regional SOCs, increasing real estate, staffing, and infrastructure costs.
- In Short: Significant investment required.
Expanding Data Centres & Cloud Infrastructure
- Why? Data localisation laws prohibit the storage of sensitive data outside certain regions.
- Cost Impact: Organisations must build new regional data centres or partner with local cloud providers, adding millions in additional IT spending.
- In Short: Major IT expenses.
Investing in Country-Specific Compliance Programs
- Why? Compliance must be tailored to each country’s cybersecurity regulations.
- Cost Impact: Organisations must increase legal and compliance spending, hiring in-house specialists and external consultants to navigate complex regulations.
- In Short: Ongoing legal costs.
Managing Multi-Region Security Architectures
- Why? Some governments restrict the use of foreign security software and require region-specific security tools.
- Cost Impact: Organisations must purchase and maintain multiple cybersecurity tools to comply with different national security policies, increasing licensing, maintenance, and operational costs.
- In Short: Higher complexity and operational costs.
Centralised vs. Decentralised: Strategic Trade-Offs
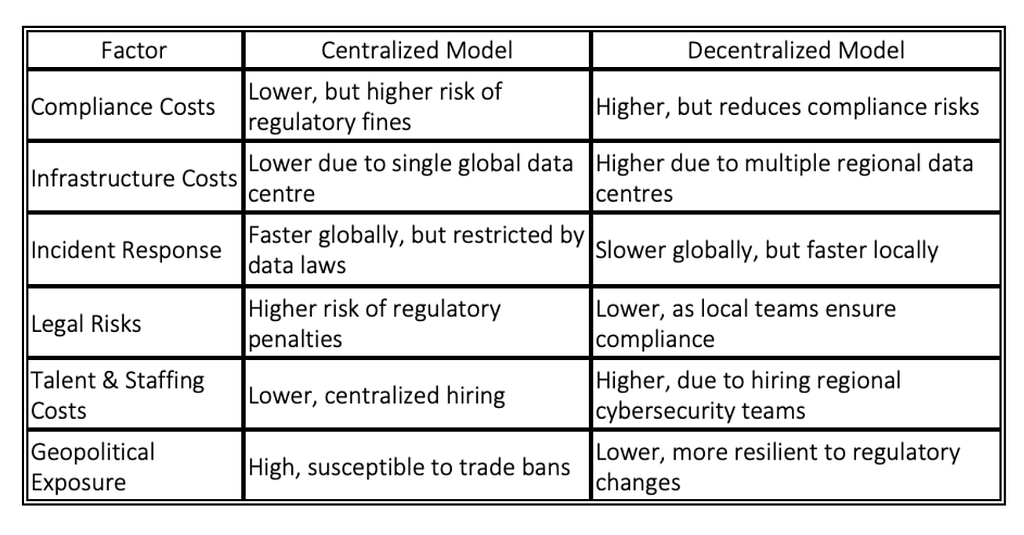
For large organisations and enterprises, the higher costs of decentralisation are a necessary trade-off to maintain market access and regulatory compliance. However, for small and mid-sized businesses, the financial burden may be unsustainable, forcing them to exit heavily regulated markets or partner with local firms instead.
What Security Leaders Must Do to Balance Cost and Risk
- Reevaluate Security Budgets – Expect higher compliance and infrastructure costs and adjust spending accordingly.
- Invest in Regional Talent – Hire cybersecurity and compliance experts in each key market.
- Build Redundant Security Infrastructures – Implement localised security solutions to meet country-specific requirements.
- Stay Agile Amid Changing Regulations – Be prepared to quickly adapt to new cybersecurity laws and geopolitical risks.
- Optimise Costs Without Compromising Security – Use hybrid models that balance centralised oversight with regional security capabilities.
To End
Cybersecurity is now a cornerstone of corporate sovereignty. The weaponisation of cyber regulations means that decentralisation is no longer optional—it’s essential.
For enterprises, the costs are high, but the risks of inaction are higher. Organisations that strategically decentralise will not only remain compliant and secure but will be more resilient, adaptive, and competitive in the new digital order.
Your cybersecurity strategy is now a geopolitical play. Are you ready to lead?
Now I want to hear from you
Tell me—how is your organisation navigating the regulatory minefield? Are you decentralising security operations, adopting a hybrid model, or holding the line with a centralised team? What’s working, what’s breaking, and where are you seeing the biggest trade-offs?
Drop your thoughts, war stories, or questions on LinkedIn as it’s where I have all my conversations. Let’s compare notes—because no one’s facing this challenge alone.
