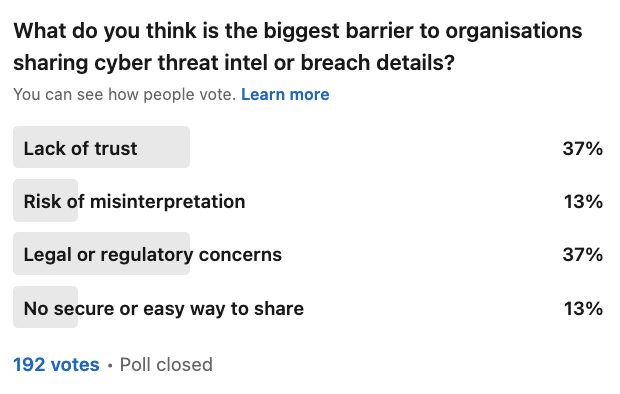
Ask yourself this question: why are hackers often more effective at collaboration than the organisations they’re targeting? This was something I did a week ago via a poll, and you can see the results here.
Recent cyberattacks on major UK retailers like Marks & Spencer, the Co-op, and Harrods by the infamous “Scattered Spider” group underline a harsh reality in cybersecurity. Hackers have mastered the art of collaboration. They share tools, tactics, and information seamlessly, with a single, aligned goal of exploiting vulnerabilities. Meanwhile, businesses often flounder in silos, stuck in a cycle of reactive IT measures and outdated perceptions of cyber risks.
But the lesson from these breaches isn’t just about better tech tools or infrastructure. It’s something much deeper and more structural that leadership must address. The real vulnerability isn’t some open port or misconfigured setting – it’s the absence of governing clarity and trust at the leadership level. And unless that changes, the cycle of high-profile breaches will continue.
The Structural Gap in Cybersecurity
The traditional boardroom narrative positions cybersecurity as an IT or compliance issue. Leadership often views it as a box to be checked or a technical challenge to be overcome. But every significant breach reveals the same critical pattern: cyberattacks are not just about technical failures. They’re a wake-up call to leadership governance.
I wrote about this recently, drawing upon Maslow’s Hierarchy of Needs to help me.
You see, the gap lies at the intersection of legal, operational, financial, and reputational consequences. Governance must transcend the boundaries of “Where is our infrastructure weak?” to answer the more profound and pivotal question, “Where are we structurally exposed to consequences?”
When trust breaks down internally or between organisations, collaboration stalls. And in cybersecurity, stalled collaboration is an open invitation for hackers to exploit the gaps. To move forward, we must redefine cyber-resilience—as not just a technical pursuit but a structural and relational one.
Humans Don’t Trust by Default But We Must Build It Anyway.
Here’s a psychological truth about trust that business leaders need to grasp: humans rarely trust unconditionally. Instead, trust operates as conditional cooperation—it’s earned gradually through credible signals like transparency, shared goals, and consistent behavior.
This is particularly evident in high-stakes environments like cybersecurity, where trust is inherently fragile. Whether it’s managing inter-organisational risks or sharing critical threat intelligence, trust becomes strategic, negotiated, and essential for success. Without it, collaboration crumbles under fear of exposure or competitive tension.
Key Barriers to Trust in Cybersecurity:
- Fear of Exposure: Sharing breach details risks reputational damage, regulatory scrutiny, or legal repercussion.
- Competitive Tension: Companies fear losing an advantage by revealing vulnerabilities to rivals. Threat intelligence can be seen as currency.
- Lack of Consistent Standards: Without shared frameworks, even willing businesses hesitate.
- Risk of Bad Actors: Trust falters when the threat of leaks or misuse looms over collaborative efforts.
Yet, trust can be built. It’s not automatic, but it can be cultivated through deliberate efforts and shared systems.
Collaboration Models That Work in Cybersecurity
Achieving trust in cybersecurity often requires combining robust frameworks with strong human relationships. Here are some that are working today for fostering collaboration across industries and organisations. Each model has trade-offs, but all recognise a central truth: trust doesn’t emerge on its own—it’s built through structure, consistency, and shared incentive.
1. Information Sharing & Analysis Centers (ISACs)
These industry-specific groups, such as FS-ISAC for financial services, provide secure forums for threat intelligence sharing.
- How They Work: These vetted membership communities operate on the Traffic Light Protocol (TLP) see below, classifying shared intelligence by its sensitivity.
- Why It Works: Vetted membership ensures reliable participation. The TLP offers a standardized way to control data dissemination. Strict governance, real-time intelligence, and reciprocal sharing establish confidence among participants.
2. Traffic Light Protocol (TLP)
A standardised method to label intelligence for ethical sharing. Information is categorized as:
- Red (Restricted sharing)
- Amber (Limited sharing)
- Green (Community-wide sharing)
- White (Public disclosure)
Why It Works: Clear guidelines reduce uncertainty around data handling, making sharing more predictable and secure.
3. Anonymised Sharing & Reciprocity Mechanisms
Techniques like anonymised breach stories lower the stakes for organisations reluctant to disclose vulnerabilities. Coupled with reciprocal expectations (e.g., “give to get”), trust accelerates as the fear of exploitation diminishes. Secure, anonymised data-sharing tools allow companies to participate without risking attribution.
Why It Works: Reduces the fear of exposure. Promotes openness in sharing breach or vulnerability information.
4. Neutral Third-Party Intermediaries
Neutral bodies like government agencies, certifying organisations, or Information Sharing and Analysis Organisations (ISAOs) extend collaborative efforts beyond traditional industry silos, creating space for broader dialogue. They provide a buffer for trust-building and can facilitate collaboration while reducing risks.
Governance bodies like the Cybersecurity Information Sharing Act (CISA) in the U.S. or ENISA in the EU provide protective frameworks:
- How They Work: Offer liability protections. Act as intermediaries for benchmarking and certification.
- Why They Work: Removes political or competitive conflicts by providing impartial governance and protections.
5. Cultural Shifts Toward Shared Responsibility
Companies that embed cyber-resilience as a shared value, rather than a competitive edge, lower barriers to trust and exhibit greater openness. Beyond frameworks, fostering human-to-human trust is equally important:
- Joint Incident Simulations — Shared tabletop exercises in cyberattacks foster rapport and alignment across partners.
- Secondments —Embedding individuals temporarily into another organization builds interpersonal trust and networks.
- “War Stories” Forums —Sharing sanitised data breaches creates learning opportunities without risking reputation.
6. Zero Trust Architecture (ZTA)
Built on the principle of “never trust, always verify,” ZTA frameworks can guide conditional and controlled data sharing between organizations.
- How It Works: Access to shared intelligence is minimized through conditional, role-based access.
- Why It Works: Trust isn’t presumed but systemically verified, allowing for sharing without undue exposure.
The Leadership Mindset Shift
The Scattered Spider Group breaches reminded us that hackers don’t just collaborate effectively; they’re ruthlessly aligned in their purpose.
Ironically, their playbook teaches enterprises a valuable lesson about the importance of trust and unified goals to counter global cyber threats.
For executives, CISOs, and boards of directors, addressing exposure isn’t just about rolling out technical controls; it’s about leading at the edge of consequence. Leaders must spearhead cultural shifts where cybersecurity is reframed as a governance priority, not an IT silo. This involves fostering a structure where trust and collaboration are embedded into every layer.
To End
I believe that by empowering more IT leaders and their execs to adopt models of conditional trust and secure collaboration, organisations can turn the tide on cyber threats. From facilitating interoperability with trusted frameworks to helping develop human-centric governance strategies, we’re here to help you lead the way.
The question isn’t whether to share or not. It’s how to share securely while staying agile and resilient. Isolation is riskier than collaboration when facing a common enemy.
Now I want to hear from you
Tell me your thoughts on this. What have you seen work? Join in the conversation on LinkedIn and let me know.
Or, if you’re a leader responsible for cyber, drop me an email or book a call and discover tools and strategies that build trust, secure data, and foster next-level collaboration across industries.
Because real resilience starts at the leadership level. Together, we can lead with trust and protect what matters most.
