Imagine building a house on sand or precariously stacking blocks in a game of Jenga. No matter how carefully you place the materials or how advanced the tools you use, the structure is doomed to collapse without a strong, stable foundation.
This is the state of cybersecurity today.
Organisations invest heavily in governance, risk, and compliance (GRC) and risk management efforts while neglecting foundational elements like leadership and culture. The result? Fragile systems that fail to keep pace with attackers.
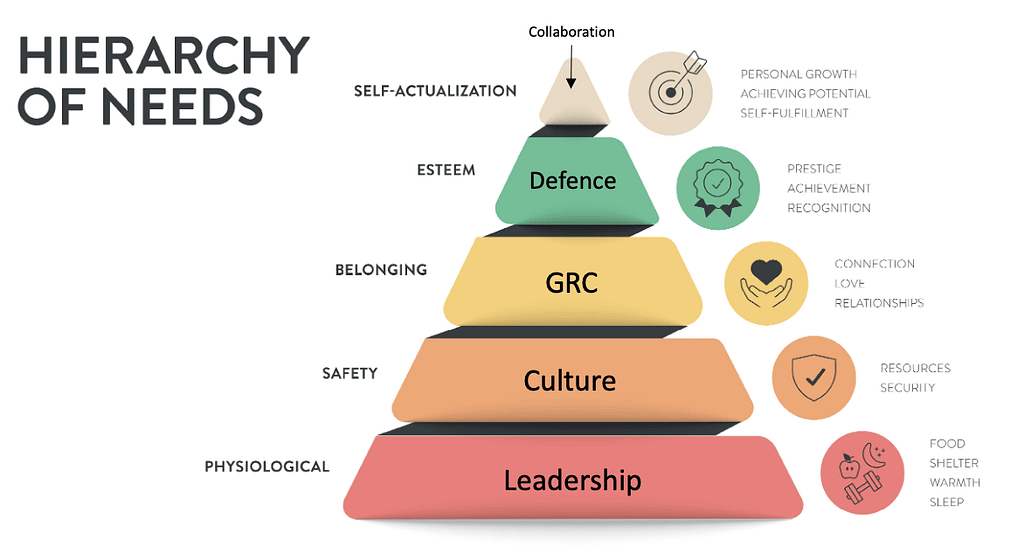
To break free from this cycle, we must rethink how we approach cybersecurity. A useful analogy is Maslow’s hierarchy of needs—a psychological framework that explains human motivation as a progression from fundamental needs to self-actualisation. Likewise, cybersecurity demands a layered approach, starting with foundational human-centered elements and building toward a resilient, secure business environment. Without these foundations, all the technology in the world won’t secure your organisation.
The Illusion of Security Built on Sand
Organisations are pouring resources into cybersecurity technologies, from generative AI to emerging quantum solutions. These tools undoubtedly offer opportunities to enhance defences, detect threats, and streamline operations. However, technology alone cannot solve the security puzzle. By focusing disproportionately on tech and GRC metrics, organisations are neglecting the deeper structural issues—much like stacking new blocks onto a shaky Jenga tower.
Consider this problem in light of Maslow’s hierarchy. Just as safety and belonging must precede human accomplishments, leadership, culture, and people-centric processes must underpin any secure environment. Without these base layers, organisations are left vulnerable, spending millions but achieving little more than an illusion of security.
The Cybersecurity Hierarchy of Needs
To secure a business—truly secure it—we need to reframe our strategies, moving away from tech-dependent approaches and focusing on what really matters. Here’s how applying the principles of Maslow’s hierarchy can transform cybersecurity:
1. Leadership Is the Foundation (Physiological Needs)
Leadership acts as the bedrock of effective cybersecurity. Strong leaders set vision, build trust, and foster accountability. Yet, today’s cybersecurity leaders often operate in a culture of fear, where asking questions feels unsafe and decisions are made with uncertainty. This weak leadership results in cracks at the very foundation of cybersecurity efforts.
To build securely, organisations must prioritise psychological safety. Teams need leaders who understand the complexity of cybersecurity and support innovation, not just compliance. When leadership is strong, the rest of the structure can rise.
2. Culture Embeds Security into Daily Life (Safety Needs)
If leadership is the foundation, culture is the frame that gives the structure its shape. A strong cybersecurity culture ensures that security isn’t just an afterthought—it becomes part of the organisation’s DNA. But too many businesses still approach cybersecurity with a compliance checklist mindset, treating it as a box to tick rather than a way to embed awareness and responsibility across the enterprise.
An effective culture prioritises continuous education, diversity of thought, and collaboration. It transforms employees into active participants in defence, rather than passive liabilities. Without this layer, even the best technology will fail because the human element is left unaddressed.
3. Risk Management Brings Clarity (Belonging and Love Needs)
The middle of the hierarchy addresses our need for connection and clarity. For organisations, this is the role of risk management. However, many businesses today drown in data, bombarded with endless alerts, metrics, and dashboards. This overload leads to analysis paralysis, distracting teams from what matters most.
Simplifying risk management through targeted metrics and actionable insights strengthens an organisation’s focus. By subtracting noise and zeroing in on critical threats, we can empower cybersecurity teams to act quickly and decisively, avoiding the chaos that often occurs during high-stress scenarios.
4. Defence Enhances Confidence (Esteem Needs)
Defence strategies are like esteem in Maslow’s hierarchy—they provide the confidence and trust that organisations need to function securely. But focusing solely on perimeter defences or siloed solutions isn’t enough. Attackers evolve constantly, and static defence mechanisms quickly become irrelevant.
Layered, adaptive security strategies that protect both operational reputation and critical assets are essential. However, these defences must also balance usability. Overly restrictive security measures can cripple operations, alienate teams, and even drive risky workarounds, which is what we regularly see.
5. Community Unlocks Purpose and Growth (Self-Actualization)
At the top of the hierarchy is community—collaboration beyond the organisation itself. When businesses engage with industry peers, share threat intelligence, and partner with external stakeholders, they elevate their security posture while contributing to a broader, safer digital ecosystem.
From cross-industry alliances to public-private partnerships, building community collaboration unlocks the full potential of a cybersecurity strategy. It transforms the fight against cyber threats from an isolated battle to a shared mission.
Technology Alone Is Not Enough
Generative AI, quantum computing, and other technological advancements offer promising possibilities, but they’re not silver bullets. Generative AI, for instance, can streamline threat detection—but it can also generate hallucinations or misuse data. Similarly, quantum computing may disrupt cryptography but also brings new vulnerabilities. Without the grounding of people and processes, such technologies can exacerbate risk rather than reduce it.
To move forward, we must place people at the centre of our cybersecurity strategies. Technology is a tool—when used in isolation, it lacks the capacity to drive meaningful change. Only by anchoring it in strong leadership, a supportive culture, and effective processes can you achieve the ultimate goal of doing business securely.
The Human Cost of Neglect
Failing to address foundational cybersecurity needs isn’t just a strategic misstep—it’s a human crisis. Overworked and overwhelmed, cybersecurity professionals face alarming rates of burnout, absenteeism, and even industry attrition. According to recent studies:
-
- 62% of cybersecurity leaders report experiencing burnout in the last 2-years, with nearly half feeling this way multiple times.
When human capacity is stretched too thin, mistakes happen. Alert fatigue, decision-making paralysis, and mental health challenges undermine the very professionals tasked with protecting your organization.
Rebuilding Cybersecurity from the Ground Up
The way forward is clear. Stop building cybersecurity strategies on the unstable sands of GRC metrics and isolated tech investments. Start with people.
Reassess your approach today. Are you missing foundational layers like leadership and culture? Are your cybersecurity strategies propped up by technology without addressing the people at their core? If so, it’s time to rebuild.
True security isn’t about doing cybersecurity better—it’s about doing business securely. This means investing in leadership, fostering a culture of security, and prioritising the health and well-being of your cybersecurity teams before layering on technology and process improvements.
To End: The Human-Centric Cybersecurity Alternative
We have a choice. Continue stacking blocks into a fragile cybersecurity Jenga tower or start building a resilient structure with strong foundations.
Emerging approaches like cybersecurity human risk management enable organizations to better measure, evaluate, and understand the behaviors and risk profiles of the humans that make up the foundational layer of truly effective cybersecurity.
Adaptive security awareness training solutions leverage individuals’ data to personalize their security awareness training, ensuring that the right person receives the right training, at the right time.
These approaches reflect the foundational insight that human-centric cybersecurity starts by putting human beings at the heart of cybersecurity, ensuring that the technology layered thereafter are compatible with the people they’re intended to protect.
The choice is simple.
Now I want to hear from you
Tell me in the comments, what’s the biggest challenge you’ve faced in getting people to engage with cybersecurity from a human risk management perspective—and how did you tackle it?
If you want to move toward a people-first cybersecurity strategy, and are unsure how to do that, join in the conversation on Linkedin or better sill schedule a discovery call.
